Unveiling The Power Of Memory Mapping: A Comprehensive Exploration Of Anonymous Mapping
Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping
Related Articles: Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping
- 2 Introduction
- 3 Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping
- 3.1 Understanding Anonymous Mapping
- 3.2 Advantages of Anonymous Mapping
- 3.3 Practical Applications of Anonymous Mapping
- 3.4 Demystifying Anonymous Mapping with Practical Examples
- 3.5 Frequently Asked Questions (FAQs)
- 3.6 Tips for Effective Anonymous Mapping
- 3.7 Conclusion
- 4 Closure
Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping

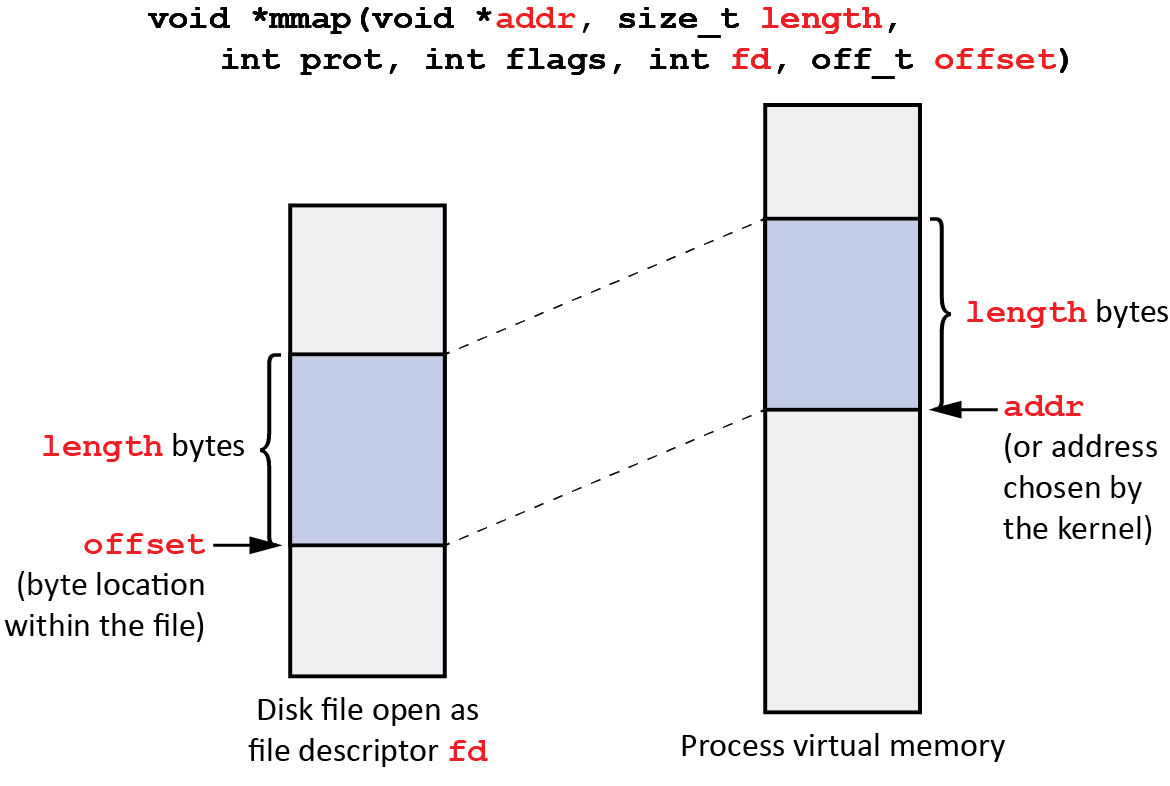
Memory mapping, a powerful technique employed by operating systems, allows programs to interact with data stored in memory directly, bypassing traditional file input/output (I/O) operations. This approach offers significant advantages in terms of performance, flexibility, and resource utilization. Within the realm of memory mapping, anonymous mapping stands out as a particularly versatile and efficient method for managing memory resources.
Understanding Anonymous Mapping
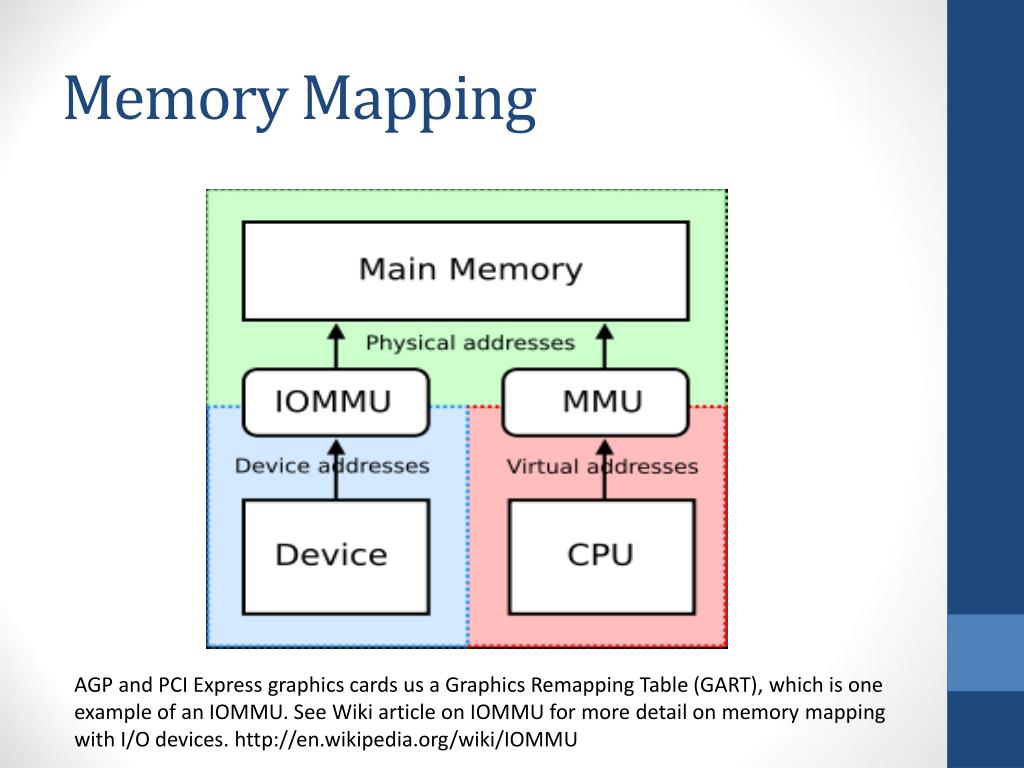
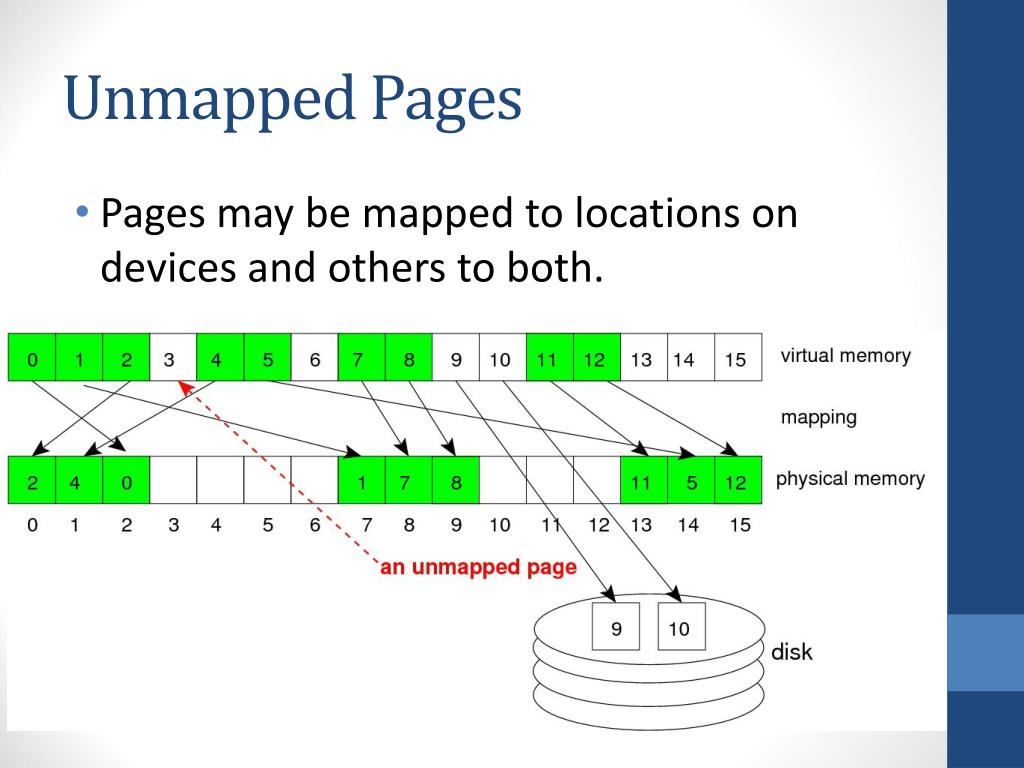
Anonymous mapping, also known as "unnamed" or "unbacked" mapping, refers to a memory mapping technique where the mapped memory region is not directly associated with a file on the file system. Instead, the operating system allocates a contiguous block of physical memory, making it accessible to the program through a virtual address space.
This approach differs from traditional memory mapping, where a file serves as the backing store for the mapped region. In anonymous mapping, the operating system manages the memory allocation and deallocation, freeing the programmer from the complexities of file I/O operations.
Advantages of Anonymous Mapping
The utilization of anonymous mapping offers several key advantages, making it a preferred technique for various programming scenarios:
- Performance Enhancement: Anonymous mapping eliminates the overhead associated with file I/O operations, leading to significant performance improvements. By directly accessing memory, programs can access and manipulate data at much faster speeds.
- Flexibility and Dynamic Memory Allocation: Anonymous mapping allows for dynamic allocation and deallocation of memory regions. This flexibility enables programs to adjust their memory footprint based on runtime requirements, efficiently managing resources and adapting to changing workloads.
- Shared Memory Communication: Anonymous mapping facilitates efficient inter-process communication (IPC) by allowing multiple processes to share the same memory region. This shared memory segment can be used for exchanging data, coordinating activities, or implementing synchronization mechanisms.
- Efficient Data Structures: Anonymous mapping provides an ideal mechanism for creating and manipulating complex data structures, such as large arrays, linked lists, or trees, directly in memory. This eliminates the need for serialization and deserialization, further improving performance and simplifying data management.
Practical Applications of Anonymous Mapping
Anonymous mapping finds extensive applications in various programming domains, including:
- High-Performance Computing: Anonymous mapping is extensively used in scientific computing, data processing, and other performance-critical applications where efficient memory management is paramount.
- Database Systems: Database systems leverage anonymous mapping for managing in-memory data structures, caching data blocks, and optimizing query execution.
- Web Servers and Network Applications: Anonymous mapping enables web servers to handle concurrent requests efficiently by maintaining shared memory regions for managing session data, request queues, and other critical resources.
- Game Development: Game engines utilize anonymous mapping to store game assets, level data, and player states in memory, enabling fast access and reducing loading times.
- Operating System Kernels: Anonymous mapping plays a crucial role in the implementation of operating system kernels, providing a mechanism for managing kernel data structures and facilitating inter-process communication.
Demystifying Anonymous Mapping with Practical Examples
To illustrate the practical applications of anonymous mapping, let’s consider a few concrete examples:
1. Implementing a Shared Memory Queue:
Anonymous mapping can be used to create a shared memory queue, enabling multiple processes to communicate and exchange data efficiently. The queue can be implemented as a circular buffer stored in a shared memory region, with processes accessing and manipulating the queue data concurrently.
2. Building a Large In-Memory Database:
Anonymous mapping provides a robust mechanism for building in-memory databases, where data is stored directly in memory for fast access. By mapping a large block of memory, the database can efficiently manage large data sets without relying on disk I/O operations.
3. Accelerating Image Processing:
Anonymous mapping can significantly enhance the performance of image processing applications by allowing direct access to image data stored in memory. This eliminates the need for file I/O operations, enabling faster image manipulation and analysis.
Frequently Asked Questions (FAQs)
1. How does anonymous mapping differ from traditional file-backed mapping?
Anonymous mapping differs from file-backed mapping in that it does not rely on a file as a backing store. Instead, the operating system allocates a contiguous block of physical memory, making it accessible to the program through a virtual address space. This eliminates the overhead associated with file I/O operations, resulting in faster access and manipulation of data.
2. What are the limitations of anonymous mapping?
While anonymous mapping offers numerous advantages, it also has certain limitations:
- Memory Management: Programmers are responsible for managing the allocated memory region, ensuring proper deallocation to avoid memory leaks.
- Security Concerns: Sharing memory regions between processes can pose security risks if proper access controls are not implemented.
- Address Space Limits: The size of the anonymous mapping is limited by the available address space of the process.
3. What is the impact of anonymous mapping on memory fragmentation?
Anonymous mapping can contribute to memory fragmentation if not managed carefully. If multiple small anonymous mappings are created and destroyed frequently, it can lead to scattered free memory blocks, reducing the efficiency of memory allocation.
4. How can I ensure the security of anonymous mapping?
To ensure the security of anonymous mapping, it is crucial to implement proper access controls and security measures. These include:
- Memory Protection: Using operating system mechanisms to restrict access to the shared memory region, preventing unauthorized modifications.
- Authentication and Authorization: Implementing robust authentication and authorization mechanisms to control access to the shared memory region based on user roles and permissions.
- Data Encryption: Encrypting data stored in shared memory regions to protect against unauthorized access or eavesdropping.
Tips for Effective Anonymous Mapping
To maximize the benefits and minimize the potential drawbacks of anonymous mapping, consider these best practices:
- Optimize Memory Allocation: Allocate memory regions based on actual requirements, avoiding excessive allocation that can lead to memory fragmentation.
- Manage Memory Deallocation: Ensure proper deallocation of memory regions when they are no longer needed to prevent memory leaks.
- Implement Access Controls: Carefully define access permissions for shared memory regions to prevent unauthorized access and maintain data integrity.
- Use Synchronization Mechanisms: Implement appropriate synchronization mechanisms, such as mutexes or semaphores, when multiple processes access the shared memory region concurrently.
- Consider Memory-Mapped Files: While anonymous mapping offers advantages in performance and flexibility, consider using memory-mapped files if persistent storage of data is required.
Conclusion
Anonymous mapping stands as a powerful technique for managing memory resources efficiently, offering significant performance gains and flexibility in various programming scenarios. By understanding its advantages, limitations, and best practices, developers can effectively leverage anonymous mapping to optimize their applications, enhance performance, and facilitate efficient inter-process communication. As technology continues to evolve, anonymous mapping will likely remain a crucial tool for optimizing resource utilization and building high-performance, scalable software systems.




Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Memory Mapping: A Comprehensive Exploration of Anonymous Mapping. We appreciate your attention to our article. See you in our next article!