Unveiling The Power Of Anonymous Memory Mapping: A Comprehensive Guide
Unveiling the Power of Anonymous Memory Mapping: A Comprehensive Guide
Related Articles: Unveiling the Power of Anonymous Memory Mapping: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Power of Anonymous Memory Mapping: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of Anonymous Memory Mapping: A Comprehensive Guide
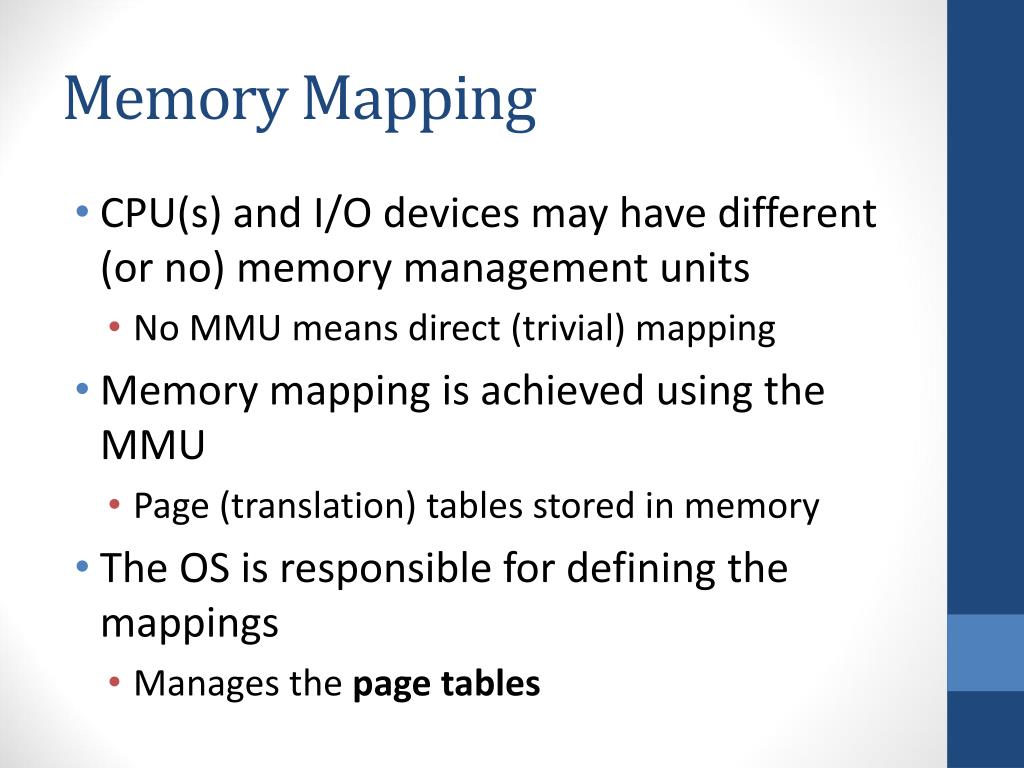
Memory mapping, a powerful technique in computer programming, allows for direct access to files and other resources within a program’s address space. This technique eliminates the need for traditional file input/output (I/O) operations, streamlining data access and boosting performance. One particularly useful variant of memory mapping is anonymous memory mapping, which allows programs to allocate and manage memory regions without associating them with specific files. This approach offers a unique set of benefits, making it an indispensable tool for a wide range of programming tasks.
Understanding the Fundamentals of Memory Mapping
Before delving into the intricacies of anonymous memory mapping, it is essential to understand the core concept of memory mapping itself. In essence, memory mapping bridges the gap between a program’s memory space and external resources, such as files. It enables the operating system to treat these resources as if they were directly accessible within the program’s address space.
This approach offers several key advantages:
- Direct Access: By mapping a file into memory, a program can access its contents directly, eliminating the need for explicit read and write operations. This simplifies data handling and reduces the overhead associated with traditional file I/O.
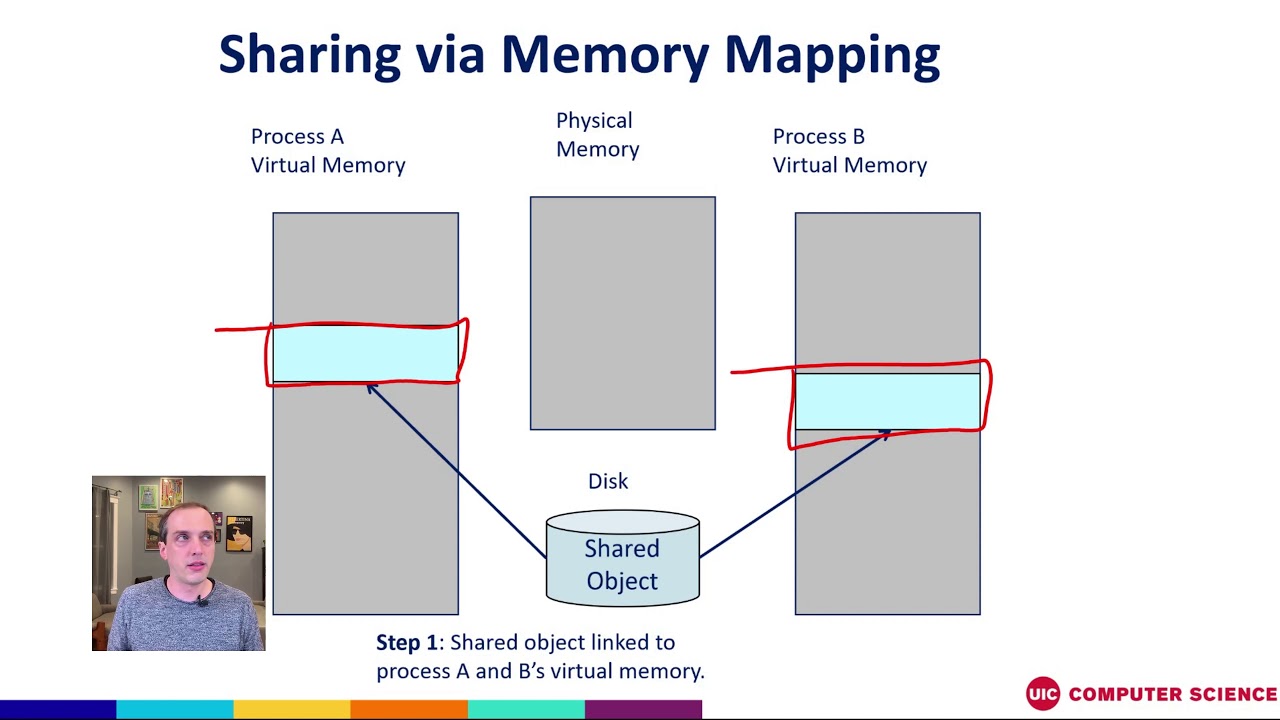
- Shared Memory: Memory mapping provides a mechanism for inter-process communication. Multiple processes can map the same file into their memory spaces, enabling them to share data efficiently. This is particularly useful for collaborative tasks and concurrent programming.
- Memory Management Simplification: Memory mapping allows the operating system to handle memory allocation and deallocation for the mapped resource. This frees up the program from managing these tasks, simplifying the development process.
The Essence of Anonymous Memory Mapping
While traditional memory mapping relies on a file as a reference point, anonymous memory mapping introduces a unique approach. Instead of associating a memory region with a specific file, it allows programs to allocate and manage memory regions independently. This creates a dedicated, private space within the program’s address space.
Key Advantages of Anonymous Memory Mapping:
- Flexibility and Control: Anonymous memory mapping provides greater flexibility in memory management. Programs can allocate and resize memory regions dynamically, adapting to changing needs. This flexibility is particularly valuable for applications that require dynamic memory allocation.
- Efficiency: By eliminating the reliance on files, anonymous memory mapping reduces the overhead associated with file system operations. This leads to improved performance, especially when dealing with large amounts of data.
- Privacy: Anonymous memory mapping ensures that data stored in these regions is not accessible to other processes or users. This enhances security and data integrity.
Applications of Anonymous Memory Mapping
Anonymous memory mapping proves to be a valuable tool across various programming domains, enabling efficient and flexible memory management. Here are some prominent applications:
- Large Data Processing: Applications that process large datasets, such as scientific simulations or data analysis tools, benefit significantly from anonymous memory mapping. It allows for efficient allocation and management of vast amounts of data within the program’s memory space.
- Shared Memory Communication: Anonymous memory mapping provides a mechanism for inter-process communication, allowing multiple processes to share data efficiently. This is crucial for collaborative tasks, such as parallel programming and distributed systems.
- Dynamic Memory Allocation: Anonymous memory mapping empowers programs to allocate and resize memory regions dynamically, adapting to changing needs. This flexibility is essential for applications that require dynamic memory allocation, such as web servers and database systems.
- Caching and Buffering: Anonymous memory mapping is ideal for implementing caching and buffering mechanisms. By creating dedicated memory regions, programs can store frequently accessed data or intermediate results, reducing the need for repeated file access.
Exploring the Practicalities of Anonymous Memory Mapping
Implementation:
Anonymous memory mapping is typically implemented using system calls provided by the operating system. For instance, in Unix-like systems, the mmap() function is used for both traditional and anonymous memory mapping. The key difference lies in the arguments passed to the function. When using anonymous memory mapping, the file descriptor argument is set to -1, indicating that no file is involved.
Example (C):
#include <sys/mman.h>
#include <stdio.h>
#include <stdlib.h>
int main()
// Allocate 1 MB of anonymous memory
void *ptr = mmap(NULL, 1024 * 1024, PROT_READ Addressing Potential Challenges:
While anonymous memory mapping offers numerous benefits, it’s crucial to be aware of potential challenges:
- Memory Management: Programs must carefully manage the memory regions allocated using anonymous memory mapping. Failure to deallocate these regions properly can lead to memory leaks and system instability.
- Security: Anonymous memory mapping requires careful security considerations, especially when dealing with sensitive data. It is important to implement appropriate access controls and security measures to prevent unauthorized access.
FAQs About Anonymous Memory Mapping:
Q: What are the differences between traditional memory mapping and anonymous memory mapping?
A: Traditional memory mapping involves associating a memory region with a specific file, allowing programs to access the file’s contents directly. Anonymous memory mapping, on the other hand, allocates memory regions without relying on files, creating a dedicated, private space within the program’s address space.
Q: When is anonymous memory mapping more suitable than traditional memory mapping?
A: Anonymous memory mapping is preferred when:
- Dynamic Memory Allocation: Applications require dynamic memory allocation, where the size of the memory region may vary during execution.
- Inter-process Communication: Multiple processes need to share data efficiently.
- Privacy: Sensitive data needs to be protected from unauthorized access.
Q: Can anonymous memory mapping be used for persistent storage?
A: Anonymous memory mapping is primarily designed for temporary storage. The data stored in anonymous memory regions is lost when the program terminates. For persistent storage, alternative methods like files or databases are recommended.
Q: What are some security considerations for using anonymous memory mapping?
A: Security considerations include:
- Access Control: Implement appropriate access controls to restrict unauthorized access to memory regions.
- Data Protection: Employ encryption or other data protection mechanisms to safeguard sensitive data stored in anonymous memory regions.
- Memory Leak Prevention: Implement robust memory management practices to prevent memory leaks and potential vulnerabilities.
Tips for Effective Anonymous Memory Mapping:
- Plan Memory Allocation: Carefully plan the size and purpose of anonymous memory regions to avoid unnecessary memory allocation and potential performance issues.
- Implement Robust Memory Management: Employ techniques like reference counting or garbage collection to ensure proper memory deallocation and prevent memory leaks.
- Consider Security Implications: Implement security measures to protect sensitive data stored in anonymous memory regions from unauthorized access.
Conclusion:
Anonymous memory mapping stands as a powerful tool for programmers seeking efficient and flexible memory management. It empowers programs to allocate and manage memory regions independently, offering numerous advantages over traditional memory mapping. By understanding its principles and applications, developers can leverage this technique to optimize their programs, enhance performance, and create robust and secure applications.

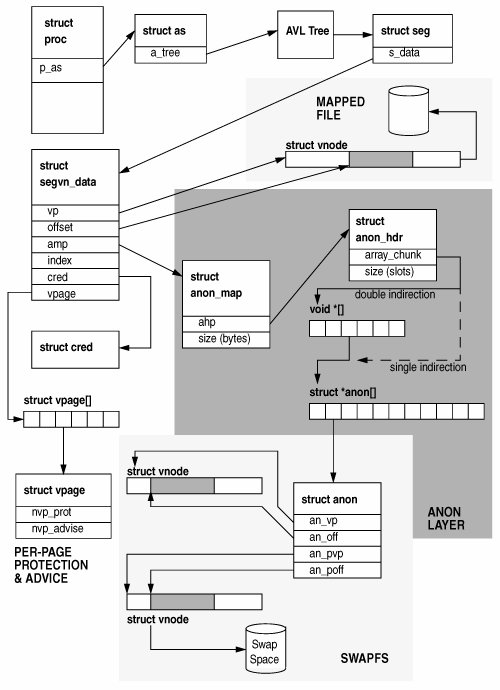
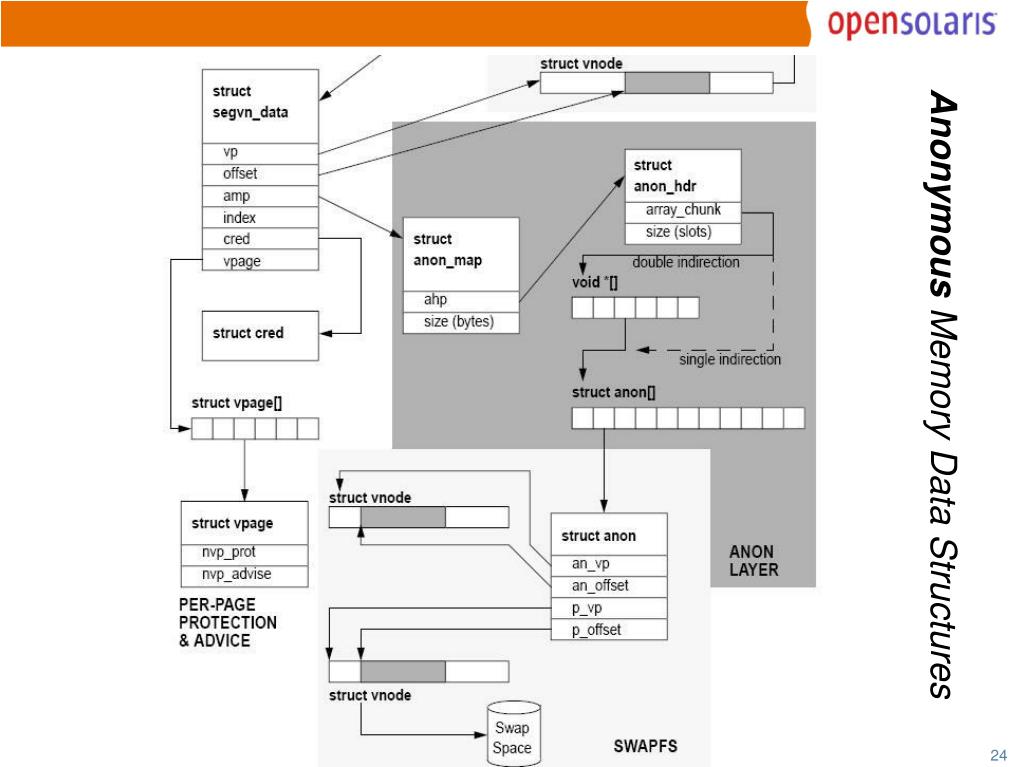

![]()
Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Anonymous Memory Mapping: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!