Unveiling Network Secrets: A Comprehensive Guide To Nmap And Zenmap
Unveiling Network Secrets: A Comprehensive Guide to Nmap and Zenmap
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap and Zenmap
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap and Zenmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling Network Secrets: A Comprehensive Guide to Nmap and Zenmap

In the intricate world of network security, understanding the architecture and vulnerabilities of systems is paramount. This is where powerful tools like Nmap and Zenmap come into play. These tools, designed for network discovery and security auditing, empower individuals and organizations to gain valuable insights into their network infrastructure and identify potential security risks.
Nmap: The Network Mapper
Nmap, short for Network Mapper, is a versatile and widely-used open-source network scanner. Its primary function is to discover hosts and services on a network, providing detailed information about their operating systems, open ports, and running services. This information is crucial for various purposes, including:
- Network Inventory: Nmap helps create a comprehensive inventory of devices connected to a network, identifying hosts, their operating systems, and the services they offer.
- Security Auditing: By scanning for open ports and vulnerable services, Nmap enables security professionals to identify potential attack vectors and weaknesses in a network.
- Network Troubleshooting: Nmap’s ability to pinpoint network devices and services aids in diagnosing network connectivity issues and identifying misconfigured devices.
Nmap offers a wide range of scanning techniques, catering to diverse needs:
- Port Scanning: This technique systematically probes network ports to identify open services. It can be customized to scan specific ports or ranges, utilizing various techniques like TCP SYN scan, UDP scan, and stealth scan.
- Operating System Detection: Nmap employs sophisticated fingerprinting techniques to identify the operating systems running on target devices. It analyzes various network characteristics, including the response times and packet sizes, to deduce the operating system with high accuracy.
- Service Version Detection: Nmap can identify the versions of services running on open ports, aiding in understanding potential vulnerabilities and security risks associated with specific service versions.
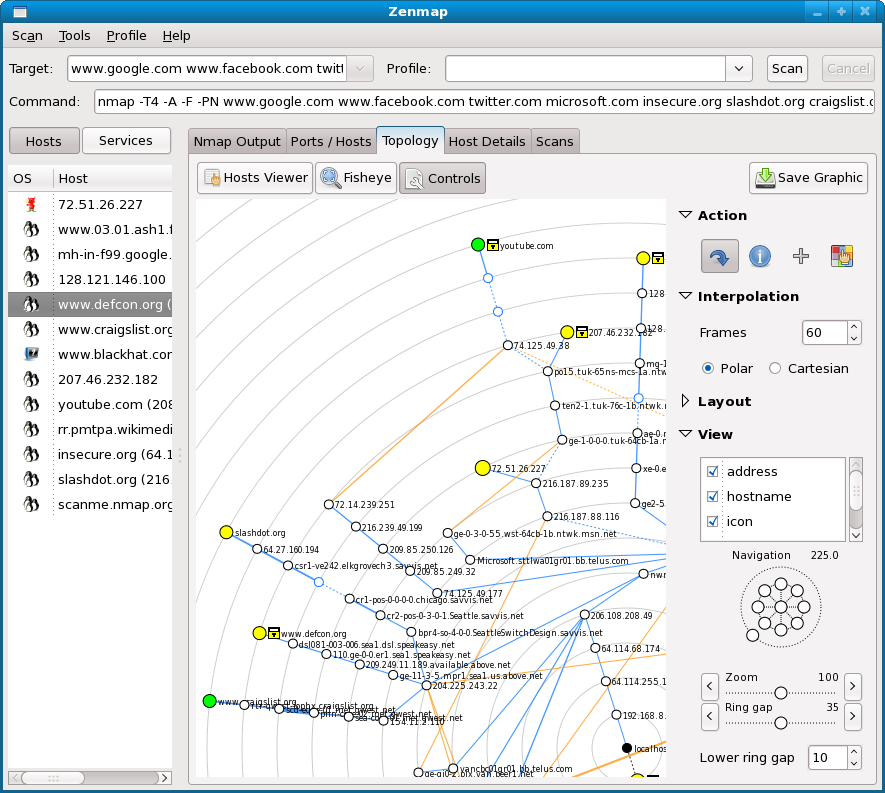
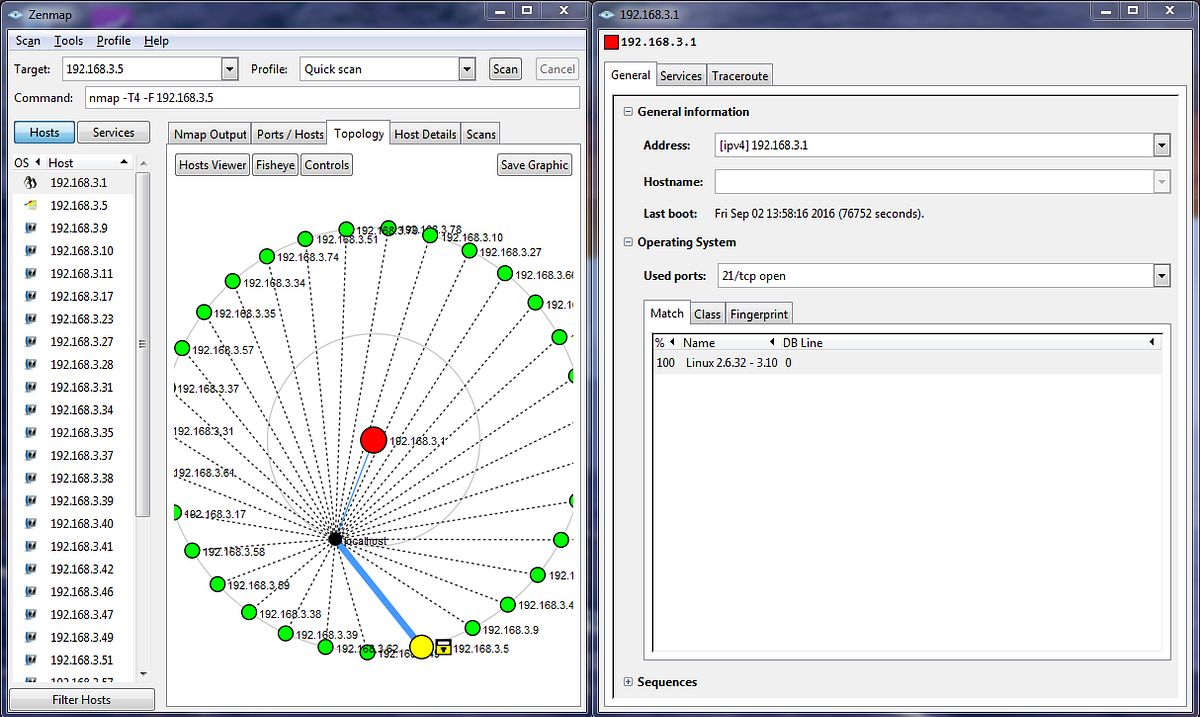
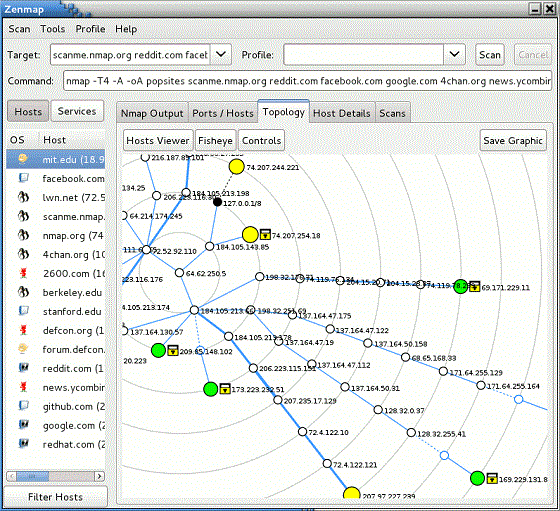
- Network Mapping: Nmap can create visual representations of network topologies, displaying the interconnected devices and their relationships within the network.
Zenmap: A User-Friendly Interface for Nmap
Zenmap is a graphical user interface (GUI) for Nmap, designed to provide a more intuitive and user-friendly experience. It offers a visual representation of scan results, making it easier to analyze data and identify key findings. Zenmap’s features include:
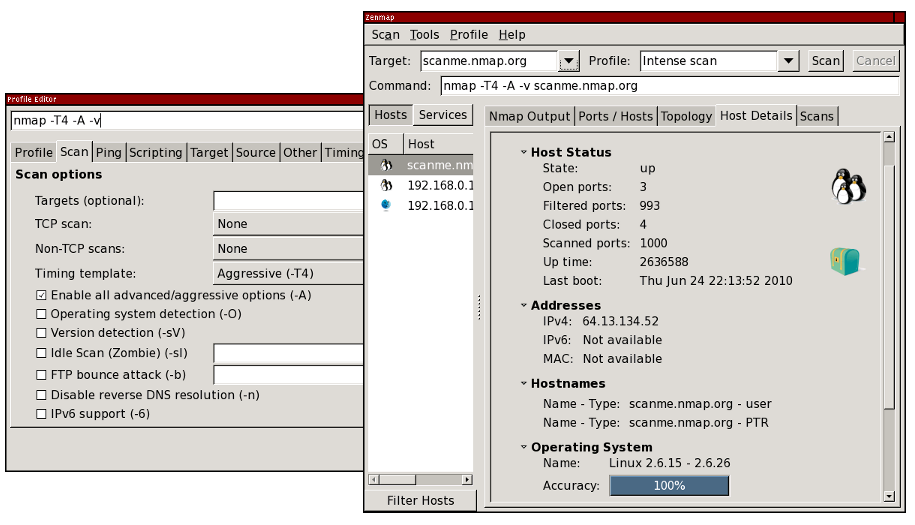
- Simplified Scan Configuration: Zenmap provides a streamlined interface for configuring and launching Nmap scans, simplifying the process for users unfamiliar with the command-line interface.
- Interactive Scan Visualization: Zenmap displays scan results in a visually appealing and informative manner, highlighting open ports, services, and operating systems.
- Report Generation: Zenmap allows users to generate comprehensive reports summarizing scan findings, facilitating easy sharing and documentation.
- Script Management: Zenmap provides a convenient way to manage and execute Nmap scripts, extending the tool’s capabilities for specific tasks and analysis.
Benefits of Using Nmap and Zenmap
The combination of Nmap’s powerful scanning capabilities and Zenmap’s user-friendly interface offers a compelling solution for various network security tasks. Their benefits include:
- Enhanced Network Visibility: Nmap and Zenmap provide a comprehensive view of network infrastructure, revealing connected devices, their operating systems, and running services. This enhanced visibility is crucial for network management and security assessment.
- Proactive Security Posture: By identifying open ports, vulnerable services, and potential attack vectors, Nmap and Zenmap enable proactive security measures to mitigate risks and enhance network resilience.
- Network Troubleshooting: Nmap’s ability to pinpoint network devices and services aids in diagnosing network connectivity issues and identifying misconfigured devices, expediting troubleshooting efforts.
- Compliance and Auditing: Nmap and Zenmap help organizations meet compliance requirements by providing detailed network information and evidence of security practices.
FAQs about Nmap and Zenmap
1. Is Nmap legal to use?
Nmap is a legitimate and widely used tool for network security professionals. However, it’s crucial to use Nmap responsibly and ethically. Scanning networks without authorization can be illegal and unethical.
2. What are the risks of using Nmap?
While Nmap is a powerful tool, it can be misused. Improperly configured scans or targeting unauthorized networks can lead to legal repercussions. Additionally, using aggressive scanning techniques can disrupt network traffic and cause performance issues.
3. What is the difference between Nmap and Zenmap?
Nmap is a command-line tool, while Zenmap is a graphical user interface for Nmap. Zenmap simplifies the process of configuring and launching scans, providing a more user-friendly experience.
4. Can I use Nmap for penetration testing?
Yes, Nmap is a valuable tool for penetration testing. Its scanning capabilities can help identify vulnerabilities and potential attack vectors, providing valuable insights for security assessments.
5. How do I learn to use Nmap effectively?
Nmap’s documentation is extensive and provides detailed information about its features and usage. There are also numerous online resources, tutorials, and training materials available to help users master Nmap’s capabilities.
Tips for Using Nmap and Zenmap
- Start with Basic Scans: Begin with simple scans to familiarize yourself with Nmap’s functionality and gradually explore more advanced techniques.
- Understand Scan Types: Familiarize yourself with the different scan types and their implications, choosing the appropriate technique for your needs.
- Configure Scan Parameters: Customize scan parameters to target specific ports, operating systems, or services, tailoring scans to your specific requirements.
- Use Scripts: Explore Nmap’s script library to extend its capabilities for specific tasks and analysis, leveraging pre-built scripts for common security assessments.
- Document Findings: Thoroughly document scan results to provide a clear record of network information and potential vulnerabilities.
Conclusion
Nmap and Zenmap are indispensable tools for network security professionals, enabling them to gain valuable insights into their network infrastructure and identify potential security risks. Their versatility, accuracy, and user-friendly interface make them powerful assets for network management, security auditing, and penetration testing. By embracing these tools and utilizing them responsibly, organizations can strengthen their security posture and protect their valuable data and systems.



Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap and Zenmap. We hope you find this article informative and beneficial. See you in our next article!