The Power Of Network Scanning: Understanding ZMap And Its Applications
The Power of Network Scanning: Understanding ZMap and Its Applications
Related Articles: The Power of Network Scanning: Understanding ZMap and Its Applications
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Power of Network Scanning: Understanding ZMap and Its Applications. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Power of Network Scanning: Understanding ZMap and Its Applications
- 2 Introduction
- 3 The Power of Network Scanning: Understanding ZMap and Its Applications
- 3.1 Understanding Network Scanning
- 3.2 The Importance of ZMap
- 3.3 ZMap on Android: Challenges and Opportunities
- 3.4 Benefits of Network Scanning on Android
- 3.5 FAQs Regarding Network Scanning on Android
- 3.6 Tips for Responsible Network Scanning on Android
- 3.7 Conclusion
- 4 Closure
The Power of Network Scanning: Understanding ZMap and Its Applications
The internet, a vast and interconnected network, is constantly evolving. With this evolution comes a need for tools that can effectively monitor, analyze, and understand its intricate structure. One such tool is ZMap, a powerful network scanner designed to probe the internet at scale, revealing crucial insights into its topology, security vulnerabilities, and the presence of specific services. While ZMap itself is a command-line tool primarily used on Linux systems, its principles and applications are readily transferable to the Android platform. This article delves into the concept of network scanning on Android, exploring the potential benefits and limitations of utilizing ZMap-like functionalities in this mobile environment.
Understanding Network Scanning
Network scanning involves sending probes to a range of IP addresses, attempting to gather information about the devices and services connected to the network. These probes can be customized to target specific ports, protocols, or services, allowing for targeted analysis. The data collected during network scanning can be invaluable for various purposes:
- Security Audits: Identifying open ports, vulnerable services, and potentially compromised devices.
- Network Mapping: Understanding the structure and connectivity of a network, including the types of devices and services present.
- Service Discovery: Locating specific services or devices based on their IP addresses or service characteristics.
- Research and Analysis: Gathering data about the internet’s infrastructure, identifying trends, and studying network behavior.
The Importance of ZMap
ZMap stands out for its ability to perform high-speed network scans at an unprecedented scale. Its key features include:
- Parallel Processing: ZMap leverages multi-core processors and distributed computing techniques to expedite scanning, enabling it to probe millions of IP addresses within a short timeframe.
- Flexible Customization: ZMap offers a wide range of options for customizing scan parameters, allowing users to tailor their scans to specific needs and targets.
- Advanced Filtering and Analysis: ZMap provides powerful tools for filtering and analyzing the collected data, enabling users to extract meaningful insights from the vast amounts of information gathered.
ZMap on Android: Challenges and Opportunities
While ZMap is primarily designed for Linux environments, its core principles can be adapted to the Android platform. However, several factors limit the direct implementation of ZMap on Android:
- Resource Constraints: Android devices typically have limited processing power, memory, and network bandwidth compared to desktop computers, potentially impacting the speed and efficiency of large-scale scans.
- Security Restrictions: Android’s security model restricts access to network interfaces and system resources, requiring specific permissions and potentially limiting the scope of scans.
- Battery Consumption: Network scanning can be energy-intensive, significantly draining device batteries. This can be a major concern for mobile devices, especially when conducting prolonged scans.
Despite these limitations, several approaches can be explored to leverage ZMap-like functionalities on Android:
- Cloud-Based Scanning: Utilizing cloud services with powerful computing resources to perform scans on behalf of Android devices. This approach allows for efficient and scalable scanning without straining device resources.
- Lightweight Scanning Libraries: Employing optimized network scanning libraries specifically designed for mobile platforms, sacrificing some scanning speed for reduced resource consumption.
- Focused Scanning: Targeting specific networks or IP address ranges, reducing the scope of scans and minimizing resource demands.
- Hybrid Approaches: Combining cloud-based scanning for large-scale scans with lightweight libraries for targeted investigations on the device.
Benefits of Network Scanning on Android
Despite the challenges, employing ZMap-like functionalities on Android can offer several benefits:
- Enhanced Security Awareness: Identifying potential vulnerabilities and compromised devices on local networks, helping users proactively protect their devices and data.
- Network Troubleshooting: Detecting network issues, identifying bottlenecks, and optimizing network performance for improved connectivity and data transfer.
- Device Discovery: Locating and managing connected devices, including IoT devices, ensuring efficient network management and security.
- Research and Development: Gathering data about network behavior and trends, providing valuable insights for network research and development.
FAQs Regarding Network Scanning on Android
Q: Is it legal to perform network scans?
A: The legality of network scanning depends on the specific context and target. Scanning public networks is generally acceptable, but scanning private networks without authorization can be illegal. It is essential to respect privacy and comply with local laws and regulations.
Q: Are there any ethical concerns regarding network scanning?
A: Network scanning can raise ethical concerns regarding privacy and security. It is crucial to use scanning tools responsibly, respecting user privacy and avoiding any malicious activities.
Q: How can I protect myself from network scans?
A: Several measures can be taken to protect against unwanted network scans:
- Firewall: Configure a firewall to block incoming connections from unauthorized sources.
- Port Blocking: Close unnecessary ports to minimize the attack surface.
- Security Software: Utilize antivirus and anti-malware software to detect and prevent malicious activities.
- Regular Updates: Keep operating systems and software up-to-date with the latest security patches.
Q: What are the risks associated with network scanning?
A: Network scanning can pose certain risks:
- Unintentional Disruption: Scanning can potentially disrupt network traffic, impacting service availability.
- Security Breaches: Malicious actors can exploit network scanning techniques to identify vulnerabilities and launch attacks.
- Legal Consequences: Performing unauthorized scans can lead to legal repercussions.
Tips for Responsible Network Scanning on Android
- Obtain Permission: Seek explicit consent before scanning private networks.
- Minimize Scan Scope: Limit scans to specific targets and avoid unnecessary probing.
- Respect Privacy: Avoid collecting or storing sensitive user data.
- Use Responsible Tools: Employ scanning tools specifically designed for ethical and responsible network analysis.
- Stay Informed: Keep up-to-date with best practices and legal regulations regarding network scanning.
Conclusion
Network scanning is a powerful tool that offers valuable insights into the internet’s structure and behavior. While ZMap itself is primarily designed for desktop environments, its principles can be adapted to the Android platform, albeit with certain limitations. By leveraging cloud-based services, lightweight libraries, and focused scanning techniques, Android users can access the benefits of network scanning, enhancing security awareness, troubleshooting network issues, and gaining valuable insights into their mobile network environment. It is crucial to approach network scanning responsibly, respecting privacy, complying with legal regulations, and employing tools designed for ethical and responsible analysis. As the internet continues to evolve, the ability to effectively scan and understand its complexities will become increasingly important, making network scanning tools like ZMap essential for navigating the digital landscape.
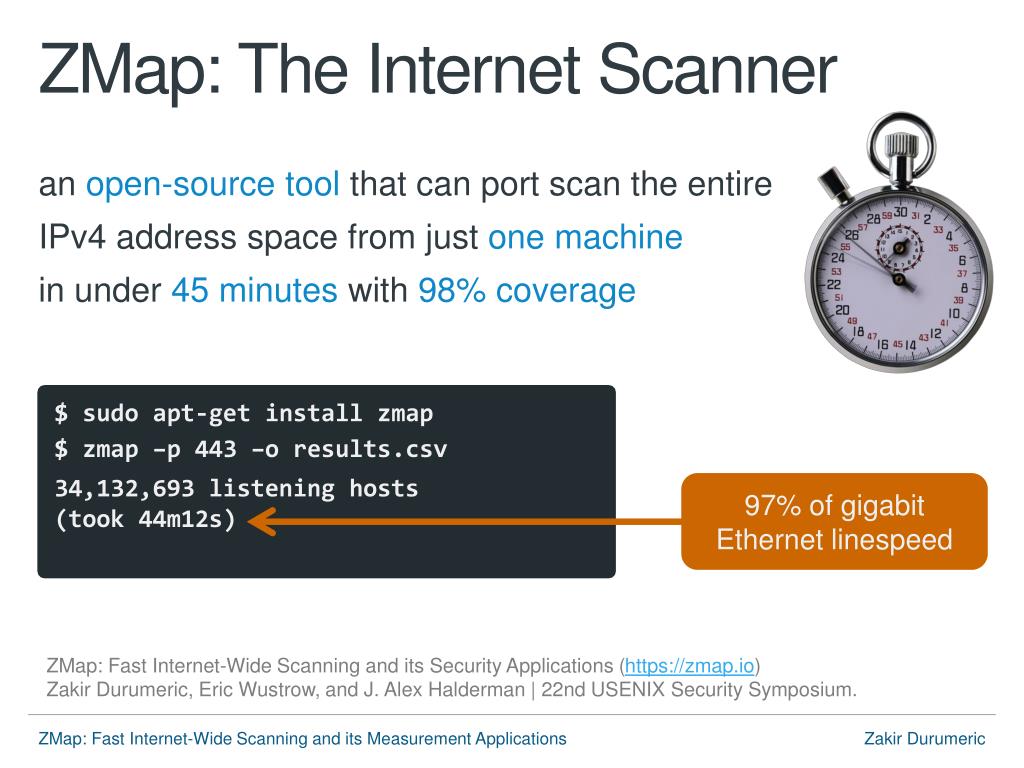



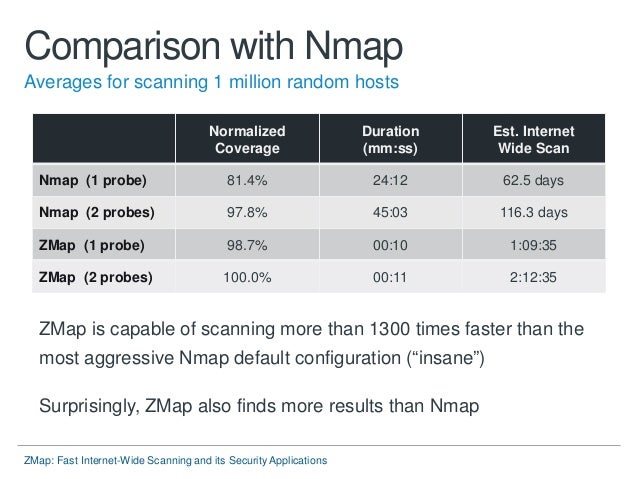

Closure
Thus, we hope this article has provided valuable insights into The Power of Network Scanning: Understanding ZMap and Its Applications. We appreciate your attention to our article. See you in our next article!