Navigating The Network Landscape: Exploring Anonymous FTP With Nmap
Navigating the Network Landscape: Exploring Anonymous FTP with Nmap
Related Articles: Navigating the Network Landscape: Exploring Anonymous FTP with Nmap
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Network Landscape: Exploring Anonymous FTP with Nmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Network Landscape: Exploring Anonymous FTP with Nmap

In the intricate world of computer networks, security and accessibility often stand in stark contrast. While firewalls and access controls safeguard sensitive data, the need to share information and resources necessitates controlled access. This delicate balance is where the concept of anonymous FTP emerges, offering a pathway for public access to specific files and data without requiring user authentication.
Understanding Anonymous FTP
FTP, or File Transfer Protocol, is a cornerstone of network communication, enabling the transfer of files between computers. In its standard form, FTP requires users to authenticate with a username and password, granting them access to specific resources. However, anonymous FTP circumvents this authentication process, allowing users to access a designated directory without providing personal credentials.
This seemingly open access is not a security loophole. Instead, it is a carefully controlled mechanism designed for specific purposes, such as sharing public data, software distributions, and documentation. Anonymous FTP servers typically restrict user access to a predefined directory, limiting their interaction to downloading files.
Nmap: A Powerful Tool for Exploring Anonymous FTP
Nmap, a network scanner renowned for its versatility and depth, plays a crucial role in exploring the world of anonymous FTP. This tool offers a comprehensive suite of capabilities, allowing users to:
- Discover FTP servers: Nmap can scan networks and identify machines running FTP services.
- Determine FTP server versions: Nmap can identify the specific FTP software running on a server, providing insights into potential vulnerabilities.
- Check for anonymous FTP support: Nmap can detect if a server supports anonymous access, revealing potential opportunities for data retrieval.
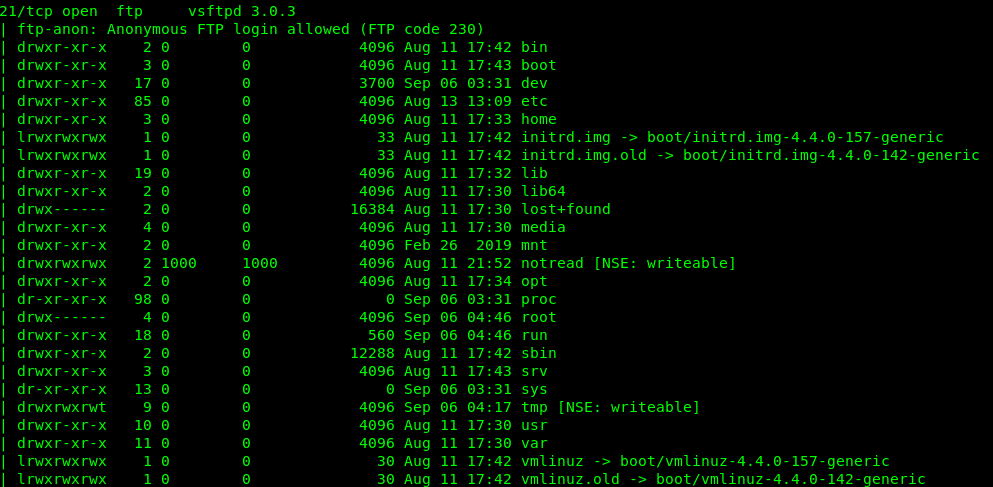
- Explore anonymous FTP directories: Nmap can list the contents of anonymous FTP directories, providing a glimpse into the available resources.
Leveraging Nmap for Exploring Anonymous FTP
Nmap’s powerful features enable a deeper understanding of anonymous FTP servers, empowering users to:
- Identify publicly available data: Nmap can reveal the existence of public data repositories, providing valuable insights into research, software, and documentation.
- Explore software distributions: Nmap can uncover FTP servers hosting open-source software distributions, offering a convenient way to access and download various programs.
- Discover technical documentation: Nmap can identify FTP servers housing technical documentation, providing valuable resources for troubleshooting, learning, and research.
- Understand security vulnerabilities: Nmap’s ability to identify FTP server versions can highlight potential security vulnerabilities, allowing for proactive mitigation efforts.
Utilizing Nmap for Anonymous FTP Exploration
Nmap’s flexibility allows for various approaches to exploring anonymous FTP, tailored to specific needs.
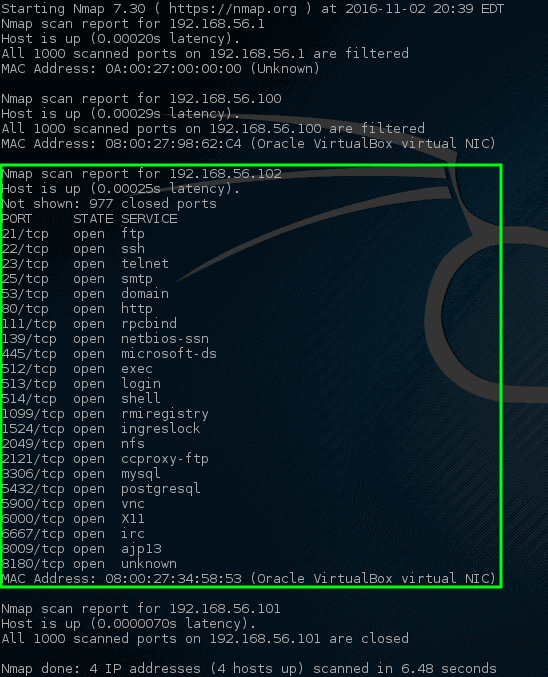
- Basic Scanning: A simple Nmap scan can identify FTP servers on a network, revealing potential targets for further investigation.
- Version Detection: Utilizing Nmap’s version detection capabilities can identify the specific FTP software running on a server, allowing for targeted analysis.
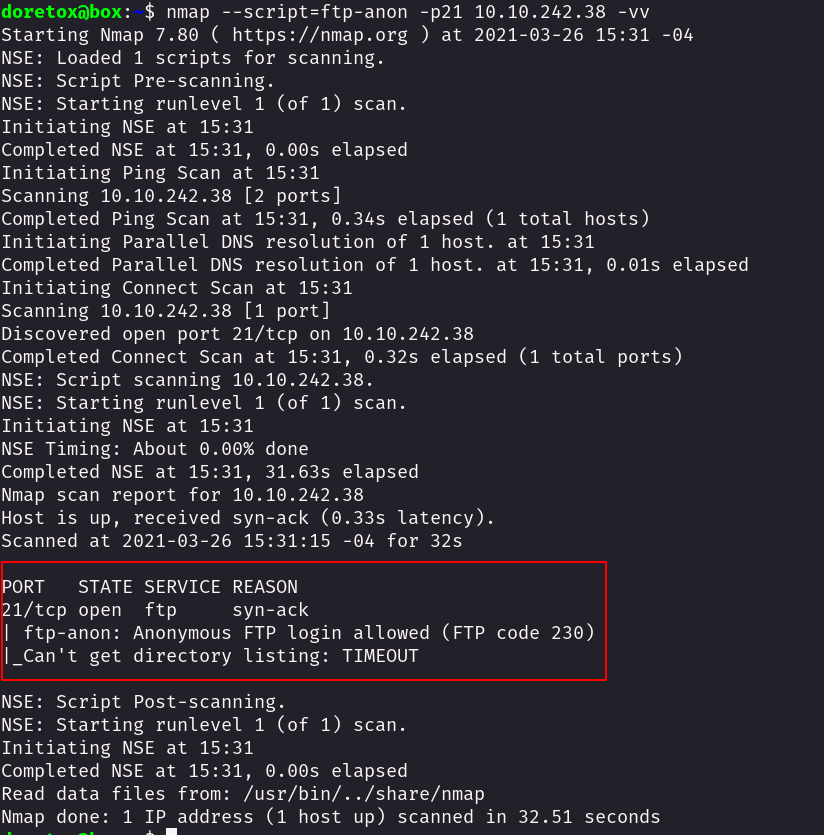
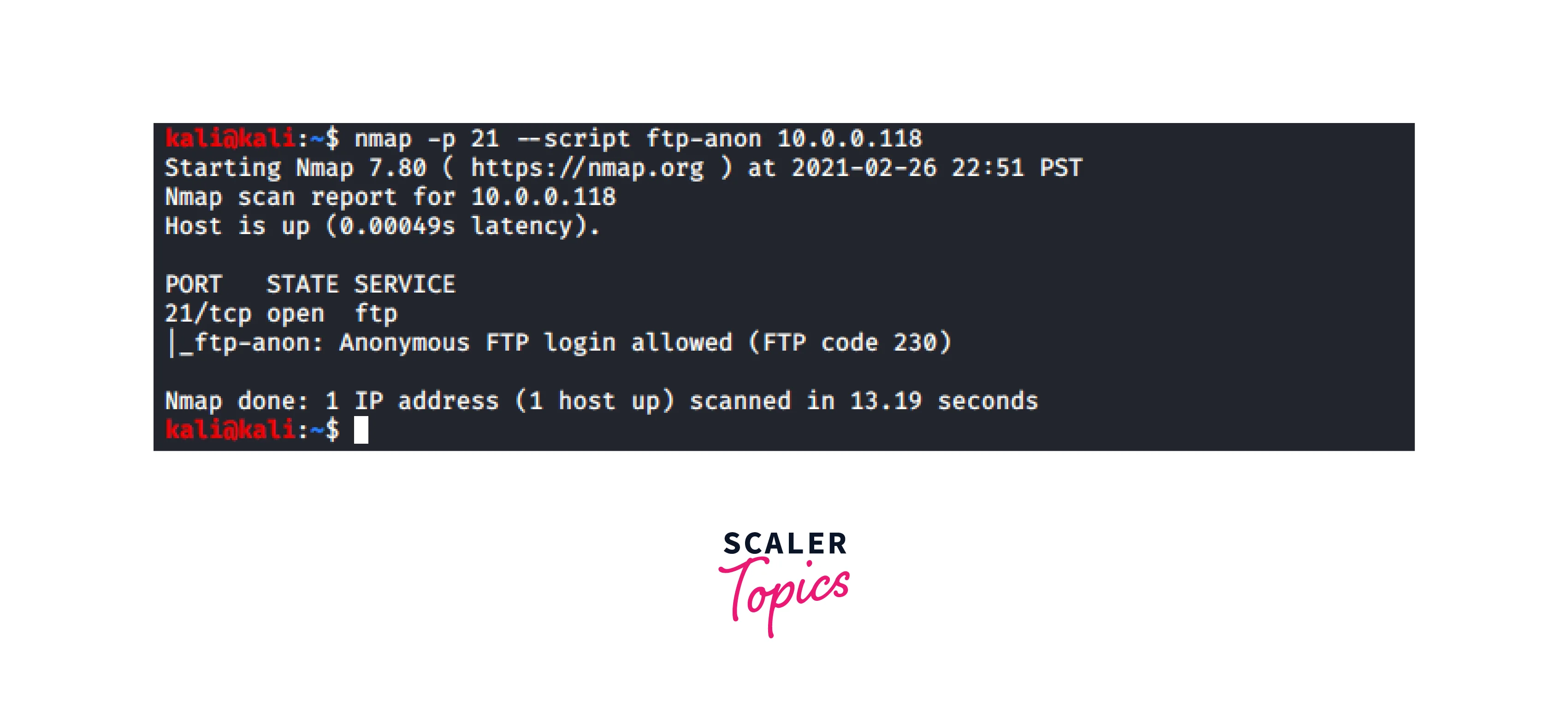
- Anonymous Access Detection: Nmap’s scripting engine can be used to detect anonymous FTP support on identified servers, highlighting potential data sources.
- Directory Enumeration: Nmap’s directory enumeration features can list the contents of anonymous FTP directories, providing a detailed overview of available resources.
Examples of Nmap Commands for Anonymous FTP Exploration
-
Basic Scan:
nmap -p 21 192.168.1.0/24(Scans the 192.168.1.0/24 network for FTP servers on port 21) -
Version Detection:
nmap -sV -p 21 192.168.1.10(Performs a version scan on the FTP server at 192.168.1.10) -
Anonymous Access Detection:
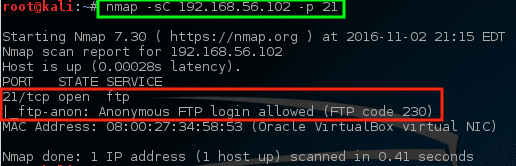
nmap -sC -p 21 192.168.1.10(Uses Nmap’s scripting engine to check for anonymous FTP support) -
Directory Enumeration:
nmap -p 21 --script=ftp-anon -oN ftp-scan.txt 192.168.1.10(Enumerates the anonymous FTP directory on the server at 192.168.1.10 and saves the results to ftp-scan.txt)
FAQs about Nmap and Anonymous FTP
Q: Is anonymous FTP always safe?
A: While anonymous FTP offers a controlled pathway for public access, it’s important to exercise caution. Always verify the source of downloaded files and be aware of potential security risks, such as malware or data breaches.
Q: Can I access any file on an anonymous FTP server?
A: No. Anonymous FTP servers typically restrict access to a designated directory, limiting user interaction to downloading files within that specific area.
Q: How can I identify legitimate anonymous FTP servers?
A: Look for reputable organizations or projects that publicly share data or software distributions. Trustworthy sources often clearly indicate the availability of anonymous FTP access.
Q: Can Nmap be used for malicious purposes with anonymous FTP?
A: While Nmap is a powerful tool for exploring anonymous FTP, it can also be misused for malicious purposes. It’s crucial to use Nmap ethically and responsibly, respecting network security and privacy.
Tips for Using Nmap with Anonymous FTP
- Start with a basic scan: Identify potential FTP servers on a network before delving into deeper analysis.
- Utilize Nmap’s scripting engine: Leverage pre-built scripts to automate tasks like checking for anonymous FTP support and directory enumeration.
- Be mindful of network security: Respect network policies and avoid scanning or accessing systems without authorization.
- Verify the source of downloaded files: Always ensure the legitimacy of downloaded files before executing or using them.
- Keep your Nmap installation updated: Regularly update Nmap to benefit from the latest security patches and feature enhancements.
Conclusion
Nmap stands as a powerful and versatile tool for exploring the world of anonymous FTP. By leveraging its capabilities, users can gain valuable insights into publicly available data, software distributions, and technical documentation. However, it’s crucial to utilize Nmap responsibly and ethically, respecting network security and privacy. Understanding the principles of anonymous FTP and employing Nmap’s features with caution can unlock valuable information and resources while navigating the complex landscape of network communication.



Closure
Thus, we hope this article has provided valuable insights into Navigating the Network Landscape: Exploring Anonymous FTP with Nmap. We hope you find this article informative and beneficial. See you in our next article!