Navigating The Landscape: A Comprehensive Guide To Java Maps
Navigating the Landscape: A Comprehensive Guide to Java Maps
Related Articles: Navigating the Landscape: A Comprehensive Guide to Java Maps
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Landscape: A Comprehensive Guide to Java Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Landscape: A Comprehensive Guide to Java Maps
Java Maps, fundamental data structures within the Java programming language, provide a powerful mechanism for storing and retrieving data in key-value pairs. Their versatility makes them indispensable tools for a wide range of programming tasks, from simple data storage to complex data analysis. This comprehensive guide delves into the various types of Java Maps, exploring their characteristics, use cases, and best practices.
Understanding the Essence of Maps
At their core, Java Maps establish a relationship between unique keys and associated values. This key-value pairing allows for efficient retrieval of data based on a specific key. Unlike arrays, which rely on numerical indices for data access, Maps offer a more flexible and intuitive approach to data organization.
Key Considerations in Choosing a Map Implementation
The choice of the appropriate Java Map implementation hinges on several factors:
- Key Type: The type of keys used in the Map plays a significant role. Some implementations are optimized for specific key types, such as strings or integers.
- Value Type: The type of values stored in the Map also influences the choice of implementation. Certain implementations are better suited for specific value types, like custom objects or primitive data types.
- Performance Requirements: The desired performance characteristics, including insertion, retrieval, and deletion speed, should be factored in. Some Map implementations offer superior performance for specific operations.
- Concurrency Considerations: If multiple threads need to access and modify the Map concurrently, thread-safe implementations are crucial to avoid data corruption.
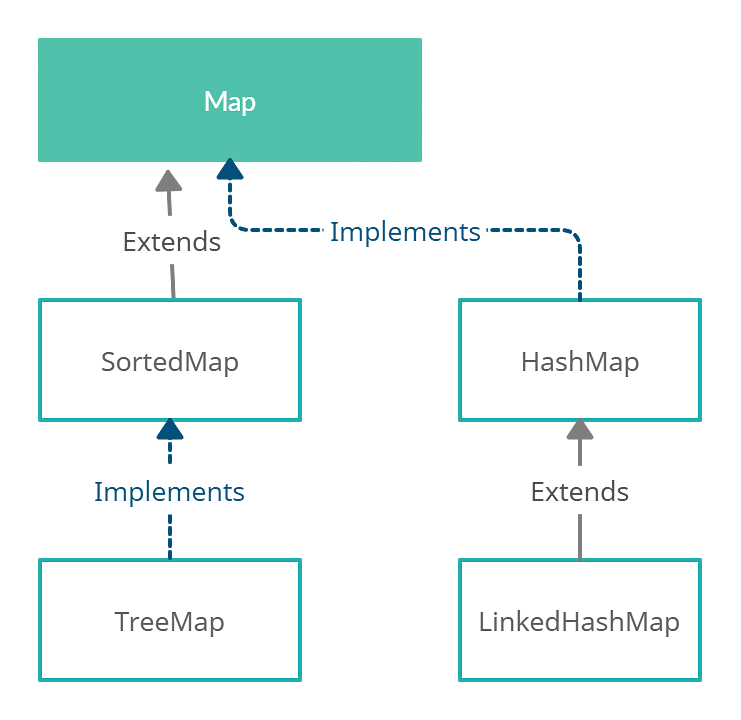
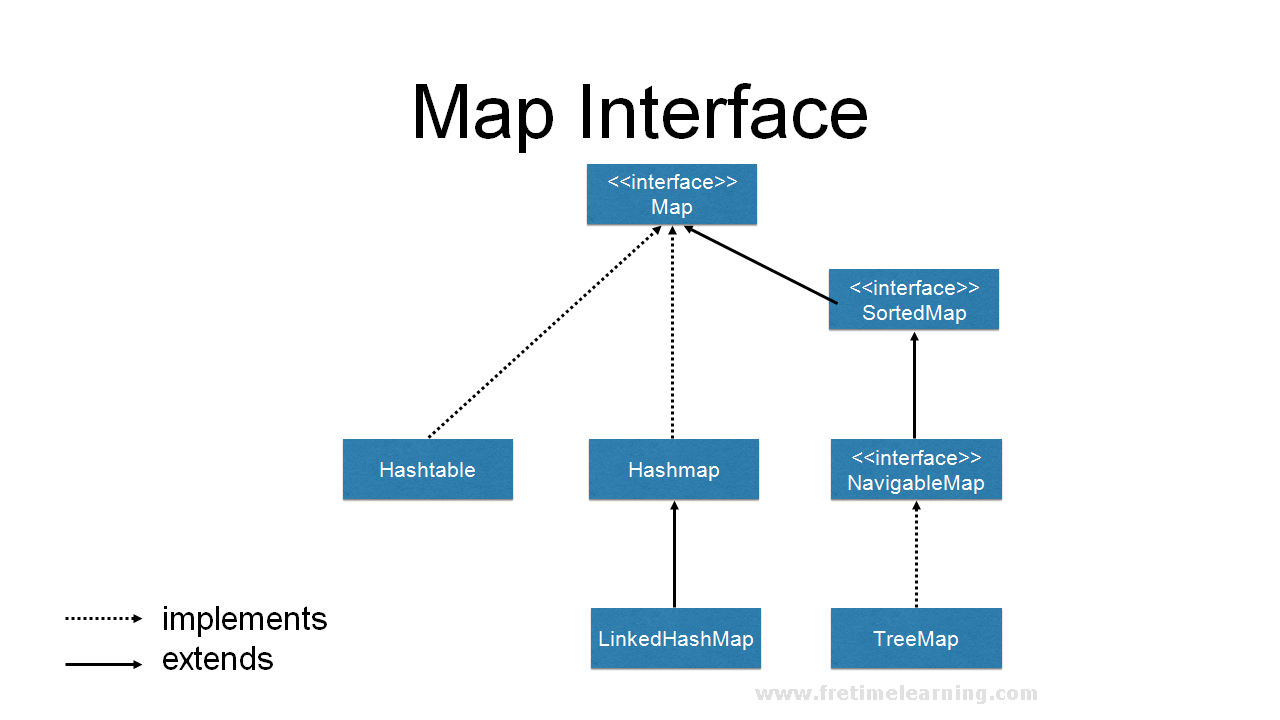
A Taxonomy of Java Maps
The Java Collections Framework provides a rich array of Map implementations, each tailored for specific scenarios. Let’s explore the most commonly used types:
1. HashMap
-
Description: The
HashMapis a fundamental and widely used implementation of theMapinterface. It uses a hash table to store key-value pairs, offering fast average-case performance for insertion, retrieval, and deletion operations. -
Key Features:
-
Unordered: Elements in a
HashMapare not stored in any specific order. -
Non-Thread-Safe: Multiple threads accessing a
HashMapconcurrently can lead to data inconsistency. UseConcurrentHashMapfor thread-safe operations. -
Allows Null Keys and Values:
HashMappermits null keys and values, but only a single null key is allowed.
-
Unordered: Elements in a
-
Use Cases:
- Storing and retrieving data based on a unique identifier.
- Implementing caches for frequently accessed data.
- Creating lookup tables for mapping values to corresponding keys.
2. LinkedHashMap
-
Description: The
LinkedHashMapextendsHashMapby maintaining the insertion order of elements. It uses a doubly linked list to track the order in which keys were inserted. -
Key Features:
- Ordered: Elements are retrieved in the same order they were inserted.
-
Non-Thread-Safe: Similar to
HashMap, it is not thread-safe for concurrent access. -
Allows Null Keys and Values:
LinkedHashMapallows null keys and values, but only a single null key is permitted.
-
Use Cases:
- Maintaining the order of elements, such as in a shopping cart or a history list.
- Implementing a least recently used (LRU) cache.
- Scenarios where preserving the insertion order is crucial.
3. TreeMap
-
Description: The
TreeMapimplements theSortedMapinterface, ensuring that elements are stored in ascending order based on their keys. It uses a red-black tree data structure, guaranteeing efficient logarithmic time complexity for most operations. -
Key Features:
- Ordered: Elements are sorted based on their keys in ascending order.
- Non-Thread-Safe: Similar to other Map implementations, it is not thread-safe for concurrent access.
-
Requires Comparable Keys: Keys must implement the
Comparableinterface or provide a customComparatorto define the sorting order.
-
Use Cases:
- Scenarios where sorted order is required, such as in a dictionary or a phonebook.
- Implementing range queries to find elements within a specific key range.
- Storing data in a naturally ordered fashion.
4. Hashtable
-
Description: The
Hashtableis an older implementation of theMapinterface. It is synchronized, making it thread-safe for concurrent access. However, its performance can be slower compared toHashMapdue to the synchronization overhead. -
Key Features:
-
Thread-Safe: Multiple threads can access and modify the
Hashtableconcurrently without data corruption. - Ordered: Elements are stored in the order they are inserted.
-
Does not Allow Null Keys or Values:
Hashtabledoes not allow null keys or values.
-
Thread-Safe: Multiple threads can access and modify the
-
Use Cases:
- Legacy applications where thread safety is a priority.
- Situations where synchronization is essential, but performance is not a critical concern.
5. ConcurrentHashMap
-
Description: The
ConcurrentHashMapis a highly efficient and thread-safe implementation of theMapinterface. It uses a segmented locking approach, allowing multiple threads to access and modify different segments concurrently. -
Key Features:
-
Thread-Safe: Multiple threads can access and modify the
ConcurrentHashMapconcurrently without data corruption. - High Performance: Offers excellent performance for concurrent operations due to its segmented locking mechanism.
-
Allows Null Keys and Values:
ConcurrentHashMapallows null keys and values.
-
Thread-Safe: Multiple threads can access and modify the
-
Use Cases:
- Applications with high concurrency requirements, such as web servers or databases.
- Scenarios where thread safety is paramount and performance is critical.
6. IdentityHashMap
-
Description: The
IdentityHashMapcompares keys using object identity rather than object equality. This means two keys are considered equal only if they are the same object, not if they have the same values. -
Key Features:
- Identity-Based Comparison: Keys are compared using object identity, not object equality.
- Non-Thread-Safe: Similar to other Map implementations, it is not thread-safe for concurrent access.
-
Use Cases:
- Situations where object identity is more important than object equality.
- Implementing weak references or caches that rely on object identity.
7. WeakHashMap
-
Description: The
WeakHashMapuses weak references for its keys. This means that if the key object is no longer referenced elsewhere in the program, it can be garbage collected. This helps avoid memory leaks by automatically removing entries whose keys are no longer in use. -
Key Features:
- Weak References for Keys: Keys are held with weak references, allowing them to be garbage collected if they are no longer referenced elsewhere.
- Non-Thread-Safe: Similar to other Map implementations, it is not thread-safe for concurrent access.
-
Use Cases:
- Implementing caches where keys are large objects that can be garbage collected when no longer needed.
- Preventing memory leaks by automatically removing entries with unreferenced keys.
FAQs by Types of Map in Java
HashMap
- Q: What is the difference between HashMap and LinkedHashMap?
-
A:
HashMapdoes not maintain the insertion order of elements, whileLinkedHashMappreserves the order in which keys were inserted. - Q: Is HashMap thread-safe?
-
A: No,
HashMapis not thread-safe. UseConcurrentHashMapfor thread-safe operations. - Q: Can HashMap have duplicate keys?
-
A: No,
HashMapdoes not allow duplicate keys. Each key must be unique.
LinkedHashMap
- Q: What is the purpose of LinkedHashMap?
-
A:
LinkedHashMapmaintains the insertion order of elements, making it suitable for scenarios where order is important. - Q: Is LinkedHashMap thread-safe?
-
A: No,
LinkedHashMapis not thread-safe. UseConcurrentHashMapfor thread-safe operations. - Q: How does LinkedHashMap maintain order?
-
A:
LinkedHashMapuses a doubly linked list to track the order in which keys were inserted.
TreeMap
- Q: What is the difference between TreeMap and HashMap?
-
A:
TreeMapmaintains elements in sorted order based on their keys, whileHashMapdoes not. - Q: Is TreeMap thread-safe?
-
A: No,
TreeMapis not thread-safe. UseConcurrentHashMapfor thread-safe operations. - Q: What are the performance characteristics of TreeMap?
-
A:
TreeMapoffers logarithmic time complexity for most operations, making it efficient for large datasets.
Hashtable
- Q: What is the difference between Hashtable and HashMap?
-
A:
Hashtableis synchronized and thread-safe, whileHashMapis not.Hashtabledoes not allow null keys or values, whileHashMapdoes. - Q: When should I use Hashtable instead of HashMap?
-
A: Use
Hashtableonly when thread safety is a priority and performance is not a major concern. In most cases,ConcurrentHashMapoffers better performance for concurrent operations. - Q: Why is Hashtable slower than HashMap?
-
A:
Hashtableis slower due to the synchronization overhead involved in ensuring thread safety.
ConcurrentHashMap
- Q: What is the advantage of ConcurrentHashMap over HashMap?
-
A:
ConcurrentHashMapis thread-safe and offers high performance for concurrent operations, making it ideal for applications with high concurrency requirements. - Q: How does ConcurrentHashMap achieve thread safety?
-
A:
ConcurrentHashMapuses a segmented locking approach, allowing multiple threads to access and modify different segments concurrently. - Q: When should I use ConcurrentHashMap?
-
A: Use
ConcurrentHashMapwhen thread safety and high performance are essential, such as in web servers or databases.
IdentityHashMap
- Q: What is the purpose of IdentityHashMap?
-
A:
IdentityHashMapcompares keys using object identity, making it suitable for scenarios where object identity is more important than object equality. - Q: How does IdentityHashMap work?
-
A:
IdentityHashMapuses object identity for key comparison, meaning two keys are considered equal only if they are the same object. - Q: When should I use IdentityHashMap?
-
A: Use
IdentityHashMapwhen object identity is crucial, such as in implementing weak references or caches that rely on object identity.
WeakHashMap
- Q: What is the purpose of WeakHashMap?
-
A:
WeakHashMapuses weak references for its keys, allowing them to be garbage collected when no longer referenced elsewhere. This helps avoid memory leaks. - Q: How does WeakHashMap work?
-
A:
WeakHashMapholds keys with weak references, meaning they can be garbage collected if no other references exist to them. - Q: When should I use WeakHashMap?
-
A: Use
WeakHashMapto implement caches where keys are large objects that can be garbage collected when no longer needed. This helps prevent memory leaks.
Tips by Types of Map in Java
HashMap
-
Tip: Use
HashMapwhen you need fast average-case performance for insertion, retrieval, and deletion operations. -
Tip: Avoid using
HashMapfor scenarios where order is important or thread safety is required.
LinkedHashMap
-
Tip: Use
LinkedHashMapwhen you need to maintain the order of elements, such as in a shopping cart or a history list. -
Tip: Consider using
LinkedHashMapto implement a least recently used (LRU) cache.
TreeMap
-
Tip: Use
TreeMapwhen you need to store elements in sorted order based on their keys. -
Tip: Ensure that keys implement the
Comparableinterface or provide a customComparatorfor defining the sorting order.
Hashtable
-
Tip: Use
Hashtableonly when thread safety is a priority and performance is not a critical concern. -
Tip: Consider using
ConcurrentHashMapfor better performance in most cases.
ConcurrentHashMap
-
Tip: Use
ConcurrentHashMapfor applications with high concurrency requirements, such as web servers or databases. -
Tip: Ensure that the
ConcurrentHashMapis properly sized to avoid contention and performance degradation.
IdentityHashMap
-
Tip: Use
IdentityHashMapwhen object identity is more important than object equality, such as in implementing weak references or caches that rely on object identity. -
Tip: Be aware that
IdentityHashMapis not thread-safe.
WeakHashMap
-
Tip: Use
WeakHashMapto implement caches where keys are large objects that can be garbage collected when no longer needed. -
Tip: Ensure that the
WeakHashMapis properly configured to avoid memory leaks.
Conclusion by Types of Map in Java
Java Maps offer a versatile and powerful mechanism for storing and retrieving data in key-value pairs. The choice of the appropriate Map implementation depends on specific requirements, including key and value types, performance characteristics, and concurrency considerations. By carefully considering these factors, developers can leverage the strengths of each Map type to optimize their applications for efficiency, scalability, and maintainability. Understanding the nuances of each Map implementation empowers developers to make informed decisions and build robust and reliable Java applications.






Closure
Thus, we hope this article has provided valuable insights into Navigating the Landscape: A Comprehensive Guide to Java Maps. We appreciate your attention to our article. See you in our next article!