A Deep Dive Into Anonymous Memory Mapping: Understanding The Power Of Mmap
A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap
Related Articles: A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap
Introduction
With great pleasure, we will explore the intriguing topic related to A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap
- 2 Introduction
- 3 A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap
- 3.1 Unveiling the Essence of Anonymous Memory Mapping
- 3.2 Advantages of Anonymous Memory Mapping
- 3.3 Applications of Anonymous Memory Mapping
- 3.4 FAQs on Anonymous Memory Mapping
- 3.5 Tips for Utilizing Anonymous Memory Mapping
- 3.6 Conclusion
- 4 Closure
A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap
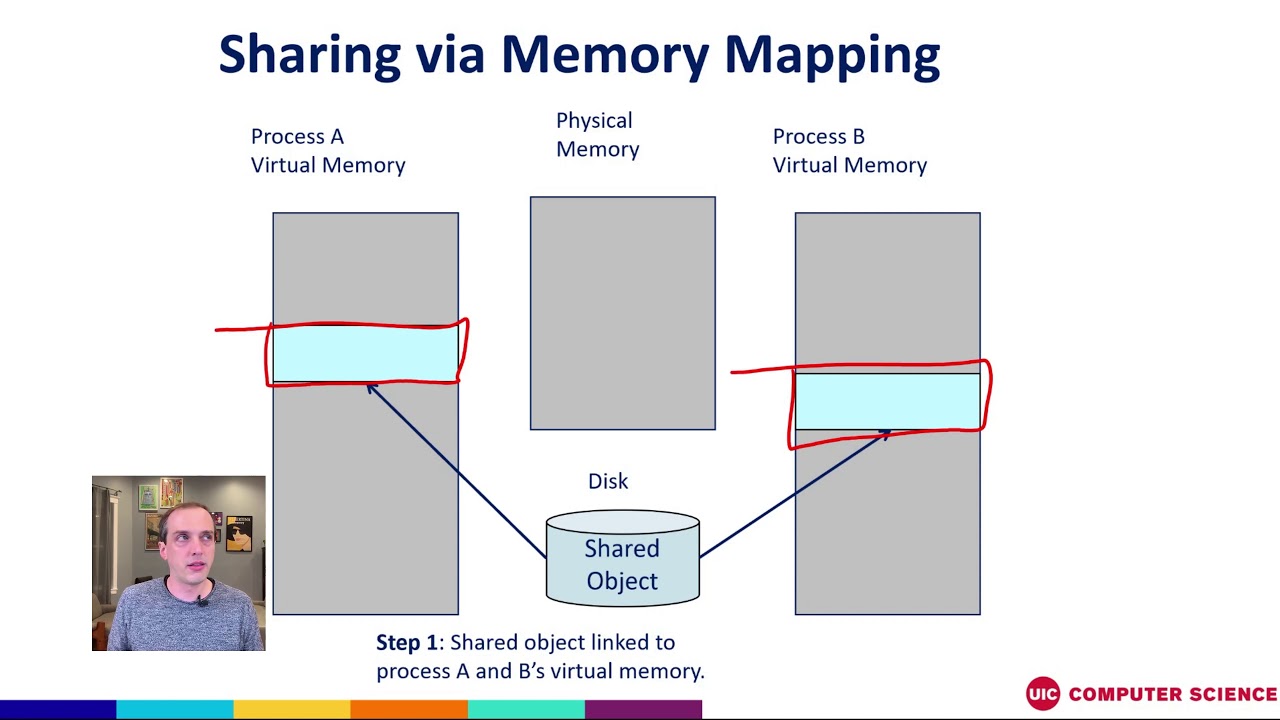
In the realm of modern operating systems, memory management plays a pivotal role in ensuring efficient resource allocation and program execution. One powerful technique employed by systems like Linux and macOS is anonymous memory mapping, commonly referred to as mmap. This mechanism provides a flexible and efficient way for processes to access and manipulate memory without the limitations of traditional file-backed memory allocation. This article delves into the intricacies of anonymous memory mapping, exploring its functionality, advantages, and practical applications.
Unveiling the Essence of Anonymous Memory Mapping
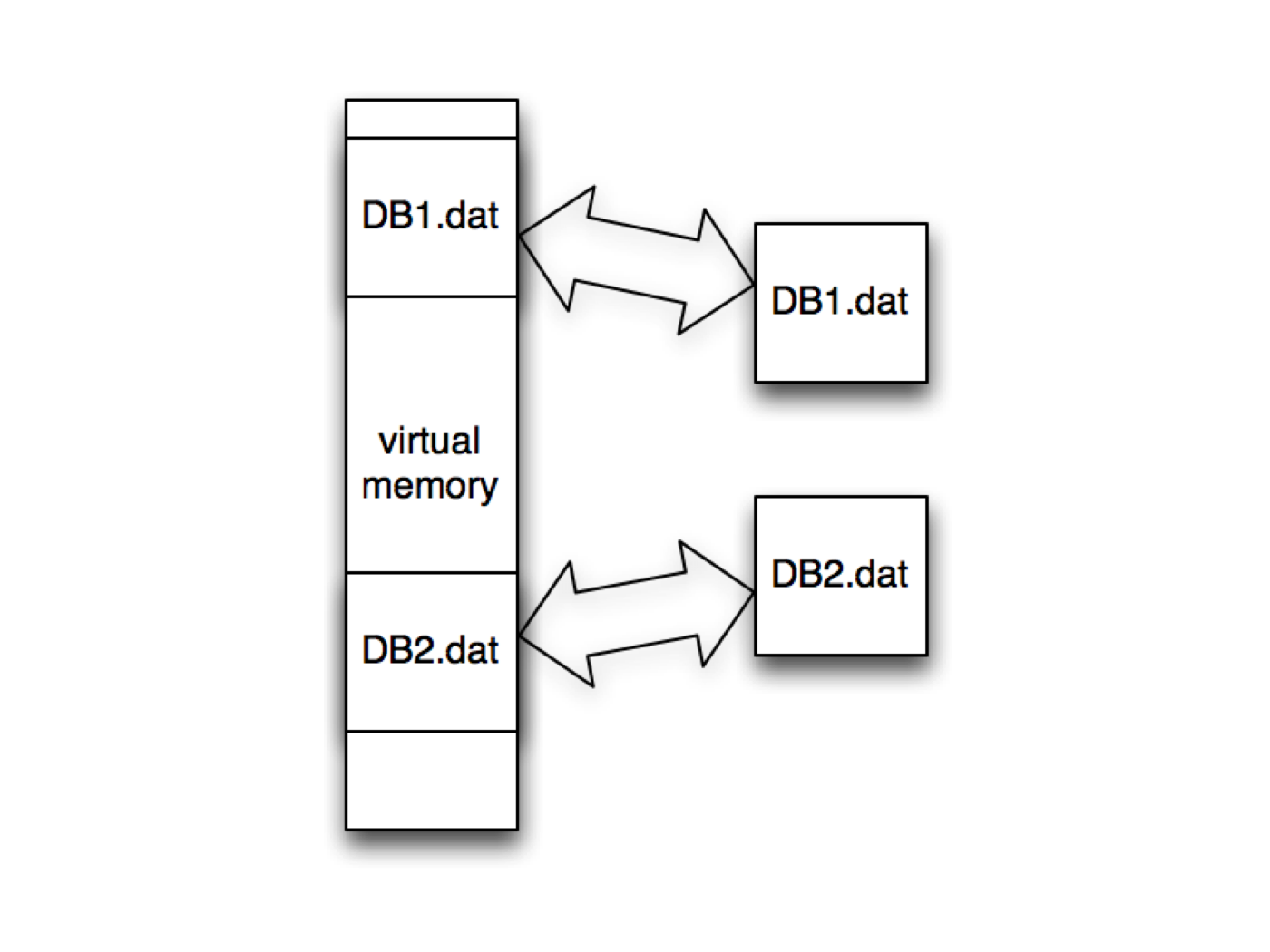
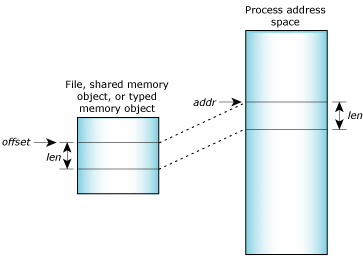
Anonymous memory mapping, facilitated by the mmap system call, allows processes to allocate and access memory regions without a direct association with a physical file on the disk. This contrasts with traditional file-backed memory mapping, where the mapped memory region is directly linked to a file, allowing for efficient data exchange between the process and the file.
In the context of anonymous memory mapping, the operating system allocates a contiguous block of virtual memory for the process, reserving it for its exclusive use. This virtual memory region is then mapped into the process’s address space, providing a direct and efficient way for the process to access and manipulate the allocated memory.
Advantages of Anonymous Memory Mapping
Anonymous memory mapping offers several compelling advantages over traditional memory allocation methods:
1. Flexibility and Efficiency:
Anonymous memory mapping provides a highly flexible and efficient way to manage memory. Processes can allocate and release memory regions dynamically, adapting to changing requirements without the overhead of file operations. This dynamic allocation allows for optimized resource utilization, minimizing memory fragmentation and improving overall system performance.
2. Reduced System Calls and Overhead:
Traditional memory allocation methods often involve numerous system calls, incurring significant overhead. Anonymous memory mapping, by allocating memory directly in the process’s virtual address space, significantly reduces the number of system calls required, thereby minimizing overhead and enhancing performance.
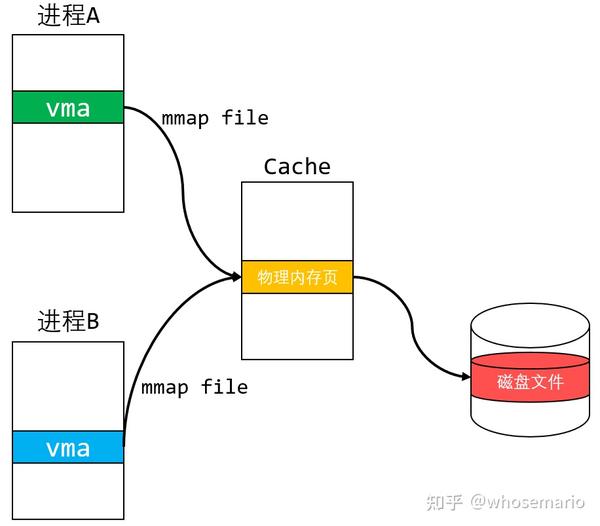
3. Shared Memory Communication:
Anonymous memory mapping enables efficient inter-process communication (IPC) through shared memory regions. Multiple processes can map the same anonymous memory region, allowing them to access and modify the shared data directly, eliminating the need for complex data exchange mechanisms.
4. Memory-Mapped Files:
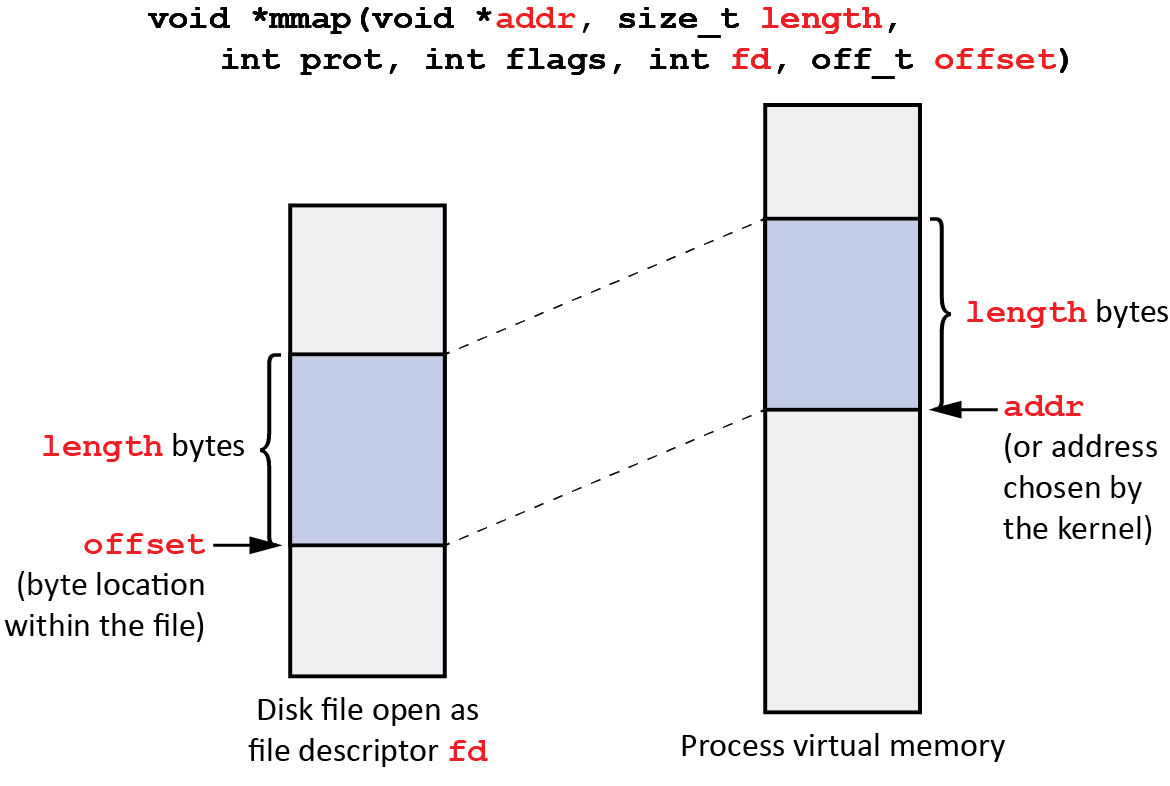
While primarily associated with anonymous memory allocation, mmap can also be used to map files into memory. This technique, known as memory-mapped files, provides a convenient and efficient way to access and manipulate file data directly in memory, eliminating the need for traditional file I/O operations.
Applications of Anonymous Memory Mapping
Anonymous memory mapping finds widespread applications in various domains, including:
1. High-Performance Computing:
In high-performance computing, where efficiency is paramount, anonymous memory mapping is extensively employed to allocate and manage large memory buffers for complex computations and data processing. This technique allows for efficient data access and manipulation, maximizing performance.
2. Database Systems:
Database systems often utilize anonymous memory mapping to manage in-memory data structures, such as hash tables and B-trees, enabling efficient data retrieval and manipulation. This approach significantly improves database performance, particularly for frequently accessed data.
3. Web Servers:
Web servers, handling numerous concurrent requests, benefit from anonymous memory mapping for managing request data, session information, and other dynamic data structures. This approach allows for efficient memory allocation and management, optimizing server performance under high load.
4. Operating System Kernels:
Operating system kernels utilize anonymous memory mapping to manage internal data structures, such as page tables and kernel stacks. This approach ensures efficient memory allocation and management within the kernel, contributing to the overall stability and performance of the system.
FAQs on Anonymous Memory Mapping
1. What is the difference between anonymous and file-backed memory mapping?
Anonymous memory mapping allocates memory directly in the process’s virtual address space without associating it with a physical file. In contrast, file-backed memory mapping maps a physical file into the process’s address space, allowing for direct access to the file’s data.
2. How does anonymous memory mapping work?
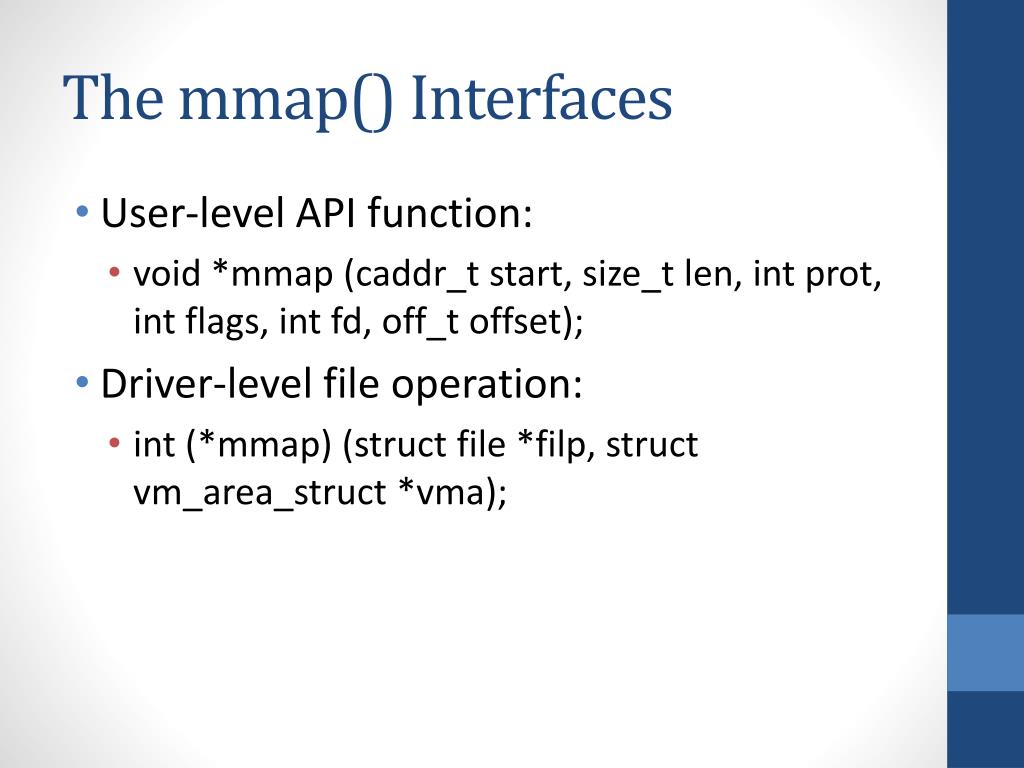
The mmap system call is used to allocate a contiguous block of virtual memory for the process. This virtual memory region is then mapped into the process’s address space, providing direct access to the allocated memory.
3. What are the advantages of using anonymous memory mapping?
Anonymous memory mapping offers flexibility, efficiency, reduced overhead, shared memory communication capabilities, and efficient memory-mapped file operations.
4. How can anonymous memory mapping be used for inter-process communication?
Multiple processes can map the same anonymous memory region, allowing them to access and modify the shared data directly. This technique facilitates efficient inter-process communication.
5. What are some common applications of anonymous memory mapping?
Anonymous memory mapping is widely used in high-performance computing, database systems, web servers, and operating system kernels for efficient memory management and communication.
Tips for Utilizing Anonymous Memory Mapping
1. Allocate Memory Efficiently:
Carefully assess the memory requirements of your application and allocate memory accordingly. Avoid excessive memory allocation, as it can lead to memory fragmentation and performance degradation.
2. Release Memory Promptly:
Release memory regions as soon as they are no longer needed. This ensures efficient memory utilization and prevents memory leaks.
3. Use Shared Memory Regions Judiciously:
Shared memory regions provide efficient inter-process communication, but they also introduce complexity. Use them strategically for specific communication needs.
4. Consider Memory-Mapped Files for Data Access:
Memory-mapped files offer efficient data access and manipulation, eliminating the need for traditional file I/O operations. Utilize this technique for large data files or frequent data access.
5. Understand the Limitations:
Anonymous memory mapping is a powerful technique, but it has limitations. Be aware of the potential for memory leaks, security vulnerabilities, and performance issues associated with its use.
Conclusion
Anonymous memory mapping, facilitated by the mmap system call, provides a versatile and efficient mechanism for managing memory in modern operating systems. This technique offers flexibility, reduced overhead, and enhanced performance compared to traditional memory allocation methods. Its applications span various domains, including high-performance computing, database systems, web servers, and operating system kernels. By understanding the principles and benefits of anonymous memory mapping, developers can leverage its power to optimize their applications and achieve improved performance and efficiency.

![MMAP Memory Mapping - [PPT Powerpoint]](https://static.fdocuments.in/doc/1200x630/5695d4fe1a28ab9b02a397ea/mmap-memory-mapping.jpg?t=1686606685)

Closure
Thus, we hope this article has provided valuable insights into A Deep Dive into Anonymous Memory Mapping: Understanding the Power of mmap. We appreciate your attention to our article. See you in our next article!